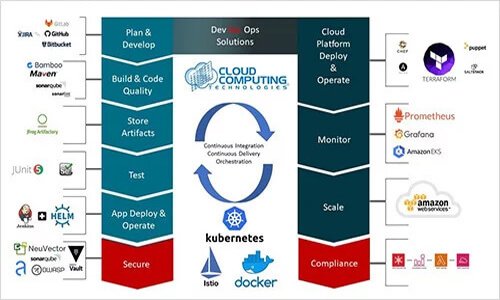
Innovative Cloud Solutions for State Agencies
In today’s rapidly evolving technological landscape, state agencies are increasingly turning towards innovative cloud solutions to streamline operations, enhance data security, and improve accessibility. Recent statistics reveal that public sector organizations embracing these technologies witness a significant transformation in their operational capabilities. This shift is driven by compelling data underscoring the tangible benefits of adopting cloud computing within the government sphere. In this blog post, we will explore seven key